Intro
Card emulation is a technique that many different RFID chips support. In this post specifically, I will use the PN532 NFC Controller chip from my USB RFID ACR122u.

RFID is divided is different categories: low frequency (LF), high frequency (HF), ultra-high frequency (UHF)… Because we have different technologies using high frequency, I will talk specifically about ISO/IEC 18000-3 which standards for Near Field Communication (NFC).
In the same way, NFC protocol is divided in three categories:
- Card emulation
- Peer to peer
- Reader/writer
I will focus on card emulation after a difficult poll:
Thinking to write a new NFC blog post…
— Salvador Mendoza (@Netxing) November 18, 2017
In order to implement a RFID reader as card emulator, we should be able to program the hardware using specific configuration commands to initialize it in that specific mode. Those commands could be Pseudo APDUs or Native orders. You can learn more about that from my first post about NFC.
Emulate a card is essential in the actual NFC technology. We can see this in almost every smart-phone or gadgets to make payments.
- Why we need to emulate a card?
To mimic a contactless card behavior, an emulation is required. Some users could implement a RFID device as contactless card to make transactions, validate an individual entrance or to access certain building or hotel. The idea of emulating is not very well documented for many different reasons. The first could be that it is difficult to implement a native language to talk to the card reader, and it changes depending of the native chip.

Moreover, the main reason to learn how to emulate a contactless card is to be prepared and aware about the dangerous scenarios and limitations of the NFC payment technology. How to test these methodologies or how to create a new NFC penetration testing tool are essential. Some of these realistic attacks using emulation were presented at DEF CON 25, for example, the Man in the NFC talk.
What do you think is going to be my next project!? #defcon pic.twitter.com/rwfU624oWL
— Salvador Mendoza (@Netxing) July 30, 2017
Of course, security by obscurity should not be implemented, instead of that, companies have to applied, in a correct way, established protocols such as distance bounding to avoid any NFC technology exploitation by relay attacks; Also a better tokenization design to protect the NFC technology against replay attacks.
- The hardware
The ACR122u is a special device. It could be implemented in different ways. I personally use it as RFID reader or emulator. To understand more about the hardware, I recommend to take a look a its datasheet.
To talk directly to the hardware, we need to use a special language: Pseudo APDU Commands + [Native Commands]. We will interchange between datasheets: the “general” AR122u and the PN532. This communication could change depending of the scenario, and sometimes we have to implement normal APDU commands or just Native Commands.
During this process, we need to answer what are the “pseudo APDU command and native command?” In the ACR122u datasheet, they describe the Pseudo APDU Commands:
- Exchanging Data with Non-PC/SC Compliant Tags.
- Retrieving and setting the reader parameters.
- The Pseudo-APDUs can be sent through the “ACR122U PICC Interface” if the tag is already connected.
- Or the Pseudo-APDUs can be sent by using “Escape Command” if the tag is not presented yet.
One thing to have in mind is that we are talking directly to the hardware, so we can access special places to extract data, even we can change behaviors in the ACR122u hardware components. This is important because with the right command, we may change the light, mode or buzzer configuration.
Establishing the Connection
As usual, I will start with a list of components to understand the process of emulation. These code examples were tested in a Mac OS 10.13.1 and Python 2.7. The Smartcard library that I am implementing with Python is pyscard to control the communication with the reader. The RFID is the USB ACR122u.
After we install the pyscard, we can test the RFID communication directly from the Python console:
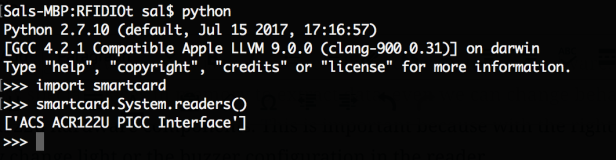
The next thing is to select what type of protocol we will use to communicate to the RFID. There are two protocols: T0 or T1. The T0 is byte-oriented half duplex transmission protocol, and the T1 is a block-oriented half duplex protocol. The T0 has a low memory capacity while the T1 has a error detection by the end of the blocks. Note: half duplex means that it can send OR transmit data only, not both tasks at the same time.

The protocol is VERY important to read the right technology. Basically, the T0 is implemented for Chip & Pin card readers, and T1 for contactless card readers. So in this case, we will select the T1.
sprotocol = smartcard.scard.SCARD_PROTOCOL_T1
Now, we have everything to create a connection to the RFID:
reader = smartcard.System.readers()
connection = reader[0].createConnection()
Assuming that we only have one connected RFID to our computer: reader[0]. At this point we are able to send commands with the established connection. To do this, we have to use the transmit() method.
result, sw1, sw2 = connection.transmit(COMMANDS,protocol = sprotocol)
We can research for special commands throughout the specification datasheets, for example, in the ACR122u we can find how to create a direct transmission to the RFID reader:

Basically, we have a class:FF, ins:00, p1:00, p2:00, the length and the data.
Summarizing: FF000000+LEN+Payload
We can do it manually and create the arrays or lists with all the commands from the datasheet, but we do not have to. Why? because Adam Laurie made that difficult task for us. In his RFIDIOt repository, we can find a complete framework with all the structures necessary to make a smooth communication to the reader. If we take a quick look at his code, we can find all the important commands from the ACR122u datasheet:

All of this section was a recap from my first and second NFC posts.
Emulation Part
Here is the tricky part. Instead of sending normal APDUs using the connection that we just created, we have to initialize the reader as emulator sending Pseudo APDU and Native commands. If we take a closer look at the Adam Laurie repository, we can find that he also has a skeleton emulation example for the PN532 chip. That code in specific is in the pn532emulate.py file.
However, the emulation part takes place with a direct interaction with the PN532 chip, for that reason we have to use the PN532 NXP datasheet to understand the initialization of Adam’s code:

From the RFIDIOt pn532emulate.py Code initializer:
status= card.acs_send_apdu(PN532_APDU[‘TG_INIT_AS_TARGET’]+mode+sens_res+uid+sel_res+felica+nfcid+lengt+gt+lentk+tk)


status= card.acs_send_apdu(PN532_APDU[‘TG_GET_DATA’])
status= card.acs_send_apdu(PN532_APDU[‘TG_SET_DATA’]+[APDU])
Running the pn532emulate.py file:
The program waits a few seconds, so we can approach a NFC reader to the RFID to start the communication. If it detects a NFC reader, the ACR122u sends a “9000”(ISO_OK) APDU command to the reader which means the last command was executed correctly:
status= card.acs_send_apdu(PN532_APDU[‘TG_SET_DATA’]+[card.ISO_OK])
#NFC payment with #PocketChip
cc @nextthingco pic.twitter.com/o7hqS9QO3X
— Salvador Mendoza (@Netxing) November 17, 2017
Sal.



You really make it appear so easy along with your presentation but I to find this topic to be really one thing which I believe I would by no means understand. It kind of feels too complex and very broad for me. I am taking a look ahead in your subsequent put up, I will attempt to get the dangle of it!
LikeLiked by 1 person
I want to create applications based on using contactless technology. I worked for over thirty years for my father in his company that built and sold its own communications concentrating server. As such, writing device driver support was an everyday thing. Your blog is SO KOOL! Thanks.
LikeLike